Key Takeaways from “How to Make DIY Security Adjustments for Cyber Threats?”
- Strengthen your passwords: Use strong, unique passwords for each account and consider employing a reputable password manager for added security.
- Enable two-factor authentication: Implement 2FA wherever possible to add an extra layer of protection and prevent unauthorized access to your accounts.
- Regularly update and monitor: Keep your software and devices up to date, and continuously monitor for any suspicious activities or anomalies to stay ahead of potential cyber threats.
Introduction
In this article, you will explore essential steps to fortify your online security and safeguard against cyber threats.
Understanding the impact of these threats is crucial in today’s digital world.
Enhancing your cyber security measures can protect your personal and sensitive data from potential breaches.
By following simple do-it-yourself adjustments, you can significantly reduce the risk of falling victim to cyber-attacks.
Stay informed about the latest practices and ensure your devices, networks, and passwords are well-protected.
Let’s dive into the actionable tips that will empower you to create a safer online environment.
Understanding Cyber Threats and Their Impact
Cyber threats encompass a wide range of malicious activities designed to exploit vulnerabilities in your digital world.
These threats include malware, ransomware, phishing, and more.
Understanding the potential impact of cyber-attacks is essential to appreciate the urgency of bolstering your security measures.
Cyber threats can lead to data breaches, financial loss, identity theft, and even reputational damage.
Stay vigilant and informed about the latest trends in cybercrime to protect yourself and your assets.
The Importance of Cyber Security Awareness
Developing a strong sense of cyber security awareness is the foundation of protecting yourself online.
Being aware of the tactics used by cybercriminals empowers you to identify and avoid potential threats.
Regularly educate yourself on phishing techniques, social engineering scams, and other common attack vectors.
Recognizing red flags and suspicious activities can make a significant difference in preventing cyber attacks.
Share your knowledge with family, friends, and colleagues to create a more secure digital community.
Assessing Your Current Cyber Security Measures
Before making any adjustments, evaluate your existing cyber security measures to identify strengths and weaknesses.
Conduct a thorough audit of your devices, networks, and online accounts.
Check for outdated software, weak passwords, and potential vulnerabilities.
Take stock of the security tools you currently have in place, such as firewalls and antivirus software.
This assessment will provide a clear picture of where improvements are needed and serve as a baseline for tracking your progress as you implement DIY security adjustments.
Identifying Vulnerabilities and Weak Points
To fortify your cyber security, it’s crucial to identify vulnerabilities and weak points in your digital infrastructure.
Conduct a comprehensive assessment of your network, devices, and online habits.
Look for outdated software, open ports, and potential entry points for attackers.
Address these weak spots promptly to minimize the risk of exploitation.
Regularly monitor and update your systems to stay ahead of evolving threats.
Implementing Strong Password Practices
One of the simplest yet most effective ways to enhance your cyber security is by using strong password practices.
Create unique and complex passwords for each of your accounts and devices.
Avoid using easily guessable information, such as names or birthdays. Instead, opt for a combination of upper and lower-case letters, numbers, and special characters.
Consider using a reputable password manager to securely store and manage your passwords.
Two-Factor Authentication: Strengthening Your Defenses
Two-Factor Authentication (2FA) is an additional layer of security that significantly strengthens your online defenses.
Enable 2FA wherever possible, as it requires you to provide a second form of verification, such as a code sent to your phone or a biometric scan.
This way, even if your password is compromised, unauthorized access will be thwarted.
Many websites and apps offer 2FA options, so make sure to take advantage of this valuable security feature.
Securing Your Home Network
Securing your home network is paramount in safeguarding against cyber threats.
Start by changing the default router login credentials to unique and robust passwords.
Enable WPA3 encryption for your Wi-Fi to protect data transmission.
Consider hiding your network name (SSID) to add an extra layer of obscurity.
Regularly update your router’s firmware to patch any known vulnerabilities.
Additionally, limit access to your network by using MAC address filtering, allowing only approved devices to connect.
Keeping Software and Devices Up to Date
Keeping your software and devices up to date is a vital aspect of maintaining strong cyber security.
Cybercriminals often exploit known vulnerabilities in outdated software.
Enable automatic updates for operating systems, web browsers, and other applications to ensure you’re always running the latest versions with improved security features.
Don’t forget about your mobile devices and IoT gadgets – they also require regular updates to stay protected against potential threats.
Educating Yourself and Your Team
Education plays a significant role in your cyber security defense strategy.
Stay informed about the latest cyber threats, attack techniques, and best practices.
Follow reputable online resources, attend webinars, and participate in cybersecurity forums to expand your knowledge.
If you run a business, educate your team about the importance of cyber security and establish clear guidelines for safe online practices.
Regularly conduct training sessions to keep everyone updated on emerging threats and reinforce security awareness throughout your organization.
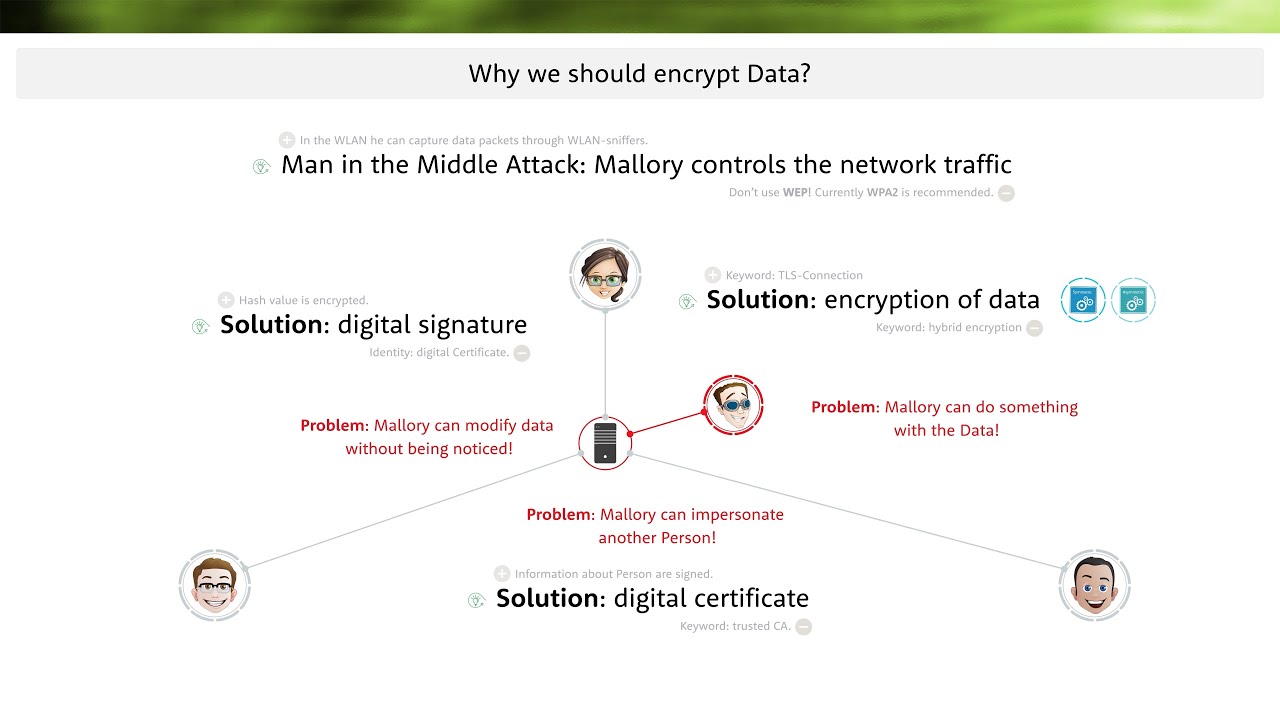
Encrypting Sensitive Data
Encrypting sensitive data adds an extra layer of protection against unauthorized access.
Use encryption software or built-in encryption features on your devices to secure important files, documents, and communications.
If you store sensitive data in the cloud, opt for services that offer end-to-end encryption to ensure data remains secure both during transmission and storage.
Regularly back up your encrypted data to prevent loss in case of a cyber incident or hardware failure.
Backing Up Critical Information
Regular data backups are a crucial aspect of cyber security.
In the event of a ransomware attack or data breach, having recent backups can prevent data loss and reduce the impact of the incident.
Use external hard drives, network-attached storage (NAS) devices, or cloud-based backup solutions to store your data securely.
Set up automatic backups to ensure you always have an up-to-date copy of your critical information.
Utilizing Virtual Private Networks (VPNs)
Virtual Private Networks (VPNs) are invaluable tools for enhancing your online privacy and security.
When using public Wi-Fi or untrusted networks, a VPN encrypts your internet traffic and routes it through a secure server, protecting your data from potential eavesdropping and cyber attacks.
Choose reputable VPN providers that prioritize privacy and do not log your internet activity.
VPNs are particularly useful when accessing sensitive information, making online transactions, or traveling abroad, where internet regulations may differ.
Avoiding Phishing and Social Engineering Attacks
Phishing and social engineering attacks are prevalent online threats, but you can protect yourself with some cautionary measures.
Be skeptical of unsolicited emails, especially those requesting sensitive information or urgent action.
Verify the sender’s email address before clicking on any links or downloading attachments.
Never share personal details or passwords through email or messages.
When in doubt, contact the supposed sender through official channels to confirm the legitimacy of the request.
Creating a Cyber Incident Response Plan
Preparing for cyber incidents is essential to minimize damage and recovery time.
Develop a comprehensive cyber incident response plan that outlines specific actions to take in case of a security breach.
Designate key personnel responsible for handling different aspects of the incident response, including communication, containment, and recovery.
Regularly test the plan through simulated scenarios to ensure your team is well-prepared to face real-life incidents.
Monitoring and Detecting Anomalies
Continuous monitoring and anomaly detection are critical for identifying potential cyber threats early on.
Implement security monitoring tools that can track network traffic, system logs, and user behavior for any unusual patterns.
Set up alerts for suspicious activities that may indicate unauthorized access attempts or data breaches.
Promptly investigate and respond to any detected anomalies to prevent potential security breaches.
Regular monitoring helps you stay vigilant and proactive in defending against cyber threats.
Employing Firewalls and Antivirus Software
Firewalls and antivirus software are essential tools for fortifying your cyber security defenses.
A firewall acts as a barrier between your network and the internet, controlling incoming and outgoing traffic based on predefined security rules.
Ensure that your router’s firewall is enabled and consider using additional software firewalls for added protection.
Antivirus software helps detect and remove malware, such as viruses, trojans, and spyware.
Install reputable antivirus software on all your devices and keep it up to date with the latest virus definitions to stay protected against evolving threats.
Understanding the Role of Employee Training
If you run a business or work in an organization, the significance of employee training in cyber security cannot be overstated.
Many cyber attacks target employees through phishing emails and social engineering techniques.
Train your employees on how to recognize and avoid such threats.
Teach them about the importance of strong password practices, data handling procedures, and how to secure their devices.
Conduct regular training sessions to keep everyone updated on the latest security measures and reinforce a culture of cyber security throughout your organization.
Empowered and informed employees can serve as a vital line of defense against cyber threats.
Conclusion
You have reached the end of “How to Make DIY Security Adjustments for Cyber Threats.”
By implementing these practical measures, you can significantly enhance your cyber security and protect yourself from potential threats.
Remember to stay vigilant, continuously educate yourself, and regularly update your devices and software.
Secure your home network, use strong passwords, and leverage two-factor authentication.
Encrypt sensitive data, back up critical information, and consider using VPNs for added protection.
Train yourself and your team to recognize and respond to cyber incidents effectively.
With these proactive steps, you can create a safer digital environment and safeguard your valuable data from cyber threats.
Stay secure and stay informed!
FAQ: How to Make DIY Security Adjustments for Cyber Threats?
1. Can I use the same password for multiple accounts?
No, it is not recommended to use the same password for multiple accounts. Using unique passwords for each account reduces the risk of multiple accounts being compromised if one password is breached.
2. How often should I update my software and devices?
Regularly update your software and devices as soon as updates become available. Cybercriminals often target known vulnerabilities, and updates include essential security patches to protect against these threats.
3. What should I do if I receive a suspicious email?
If you receive a suspicious email, avoid clicking on any links or downloading attachments. Verify the sender’s email address and contact the supposed sender through official channels to confirm the legitimacy of the email.
4. Is two-factor authentication necessary?
Yes, two-factor authentication (2FA) is highly recommended. It adds an extra layer of security by requiring a second form of verification, such as a code sent to your phone, in addition to your password.
5. How often should I back up my data?
Regular data backups are essential. Depending on the frequency of data changes, consider scheduling daily, weekly, or monthly backups to ensure you always have an up-to-date copy in case of a cyber incident.